Current Case Files
Case File 0.1

It is 1867. America is still reeling from the after-effects of a bitter civil war. The South is struggling to adapt and reconcile to the new reality of federal co-existence while the North is striving to establish a new economy, reintegrating the secessionists and establishing the civil rights of the newly freed slaves.
In this fervid atmosphere political tensions ran high. It was a VERY strange time to embark on a book signing tour, possibly the worst time. But also possibly the best time. It all depended on what his tour was for. And that has remained secret for over 150 years. Your task is to unravel the secret, or secrets , behind his mission!
Case file 1.1

Grenville M. Dodge was an ex soldier and engineer who made his fortune in the reconstruction after the civil war. From his letter to Dickens it seems that he had a social conscience, but perhaps that is not surprising for someone who dedicated himself to the unionist cause and all it stood for. He seems to have been a friend or acquaintence of Charles Babbage, which perhaps suggests that there might be something more to his letter, but only time will tell!
Case file 1.2

Sometimes a guess as to who sent a message is all you need to get started breaking the cipher! Notice how the X and Z in this fragment at the end of the cipher text line up with the G and the E in the General’s name! What does that suggest?
Case file 2.1

It is always worth checking the text at the start and end of a message to see if there are any suggestive patterns. In this case our correspondent has laid out the letter in traditional style, so perhaps this is his signature? Does that help at all? You could also look for three letter words and take a guess that they are AND or THE to see if that gives you more of the text, though knowing this is an affine shift cipher allows you to also be a little more systematic if you want!
Case file 2.2

Since we already know that Babbage wrote the letter, the pattern IFIIF (reflecting the pattern babba in the name) is really suggestive. Whatever cipher has been used to create the message probably encrypts A as F and B as I. But that is not all we have. Your BOSS training staff have also told you that the cipher is an affine shift cipher, so this is the affine shift that moves A to F and B to I. As F and I are 3 apart in the alphabet and a and b are 1 apart, this tells you that the multiplication factor in the cipher must be 3! That really cuts down the possibilities.
Case file 3.1
The transposition cipher used in part B splits text into blocks which are each permuted, usually all the same length and in the same way. But this text has 728 characters and that only factorises as 2×364. Blocks of length 2 are very unlikely and blocks of length 364 would be totally impractical. It looks like something is wrong, or perhaps missing. 729 = 3^6, so perhaps the blocks have length 3 or 6, but it is more likely that there are two characters missing and the text had 730 characters. 730 = 2x5x73 and blocks of 5 work very well for the rest of the message. That leaves us to decide what could go at the end. If you look at this image of the original letter you can see what might have happened. It looks like the letter writer was comfortable using spaces as padding characters and the clerk who typed the transcript for the archive didn’t think they were important. In this case they really were!
Good luck, Jodie.
Case file 3.2
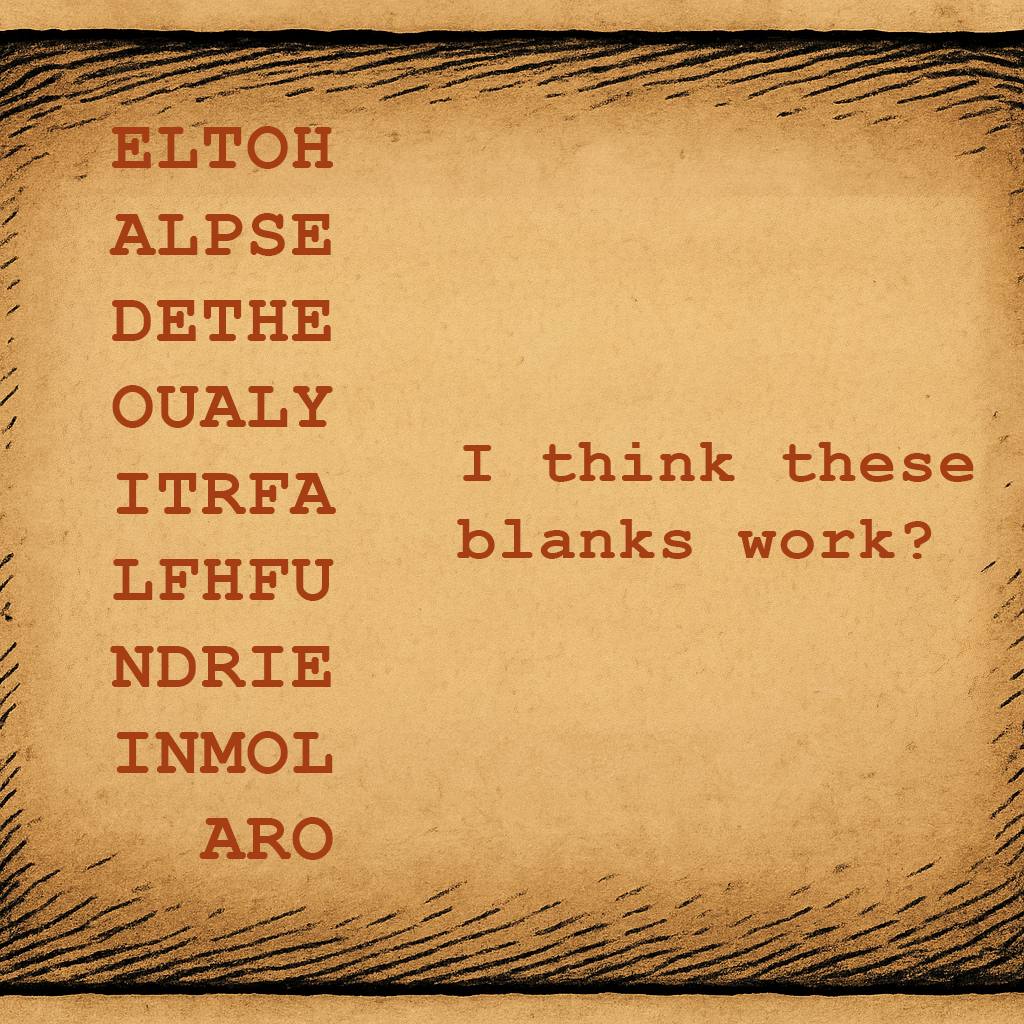
Here is my interpretation of how to write the text to decipher it. I think this works!
Good luck, Jodie.
Case file 3.3

By popular demand here is another hint about how to tackle this cipher!
Good luck, Jodie.
Case file 4.1
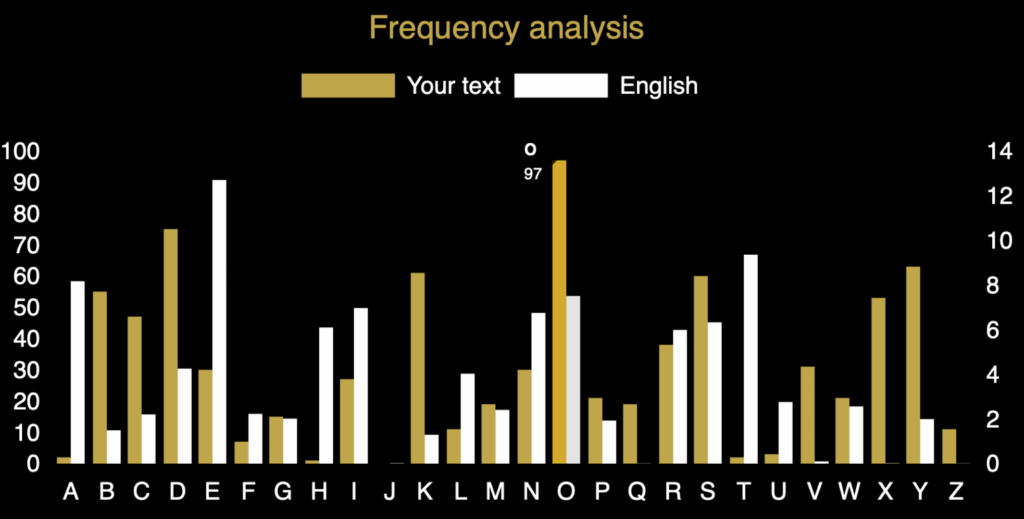
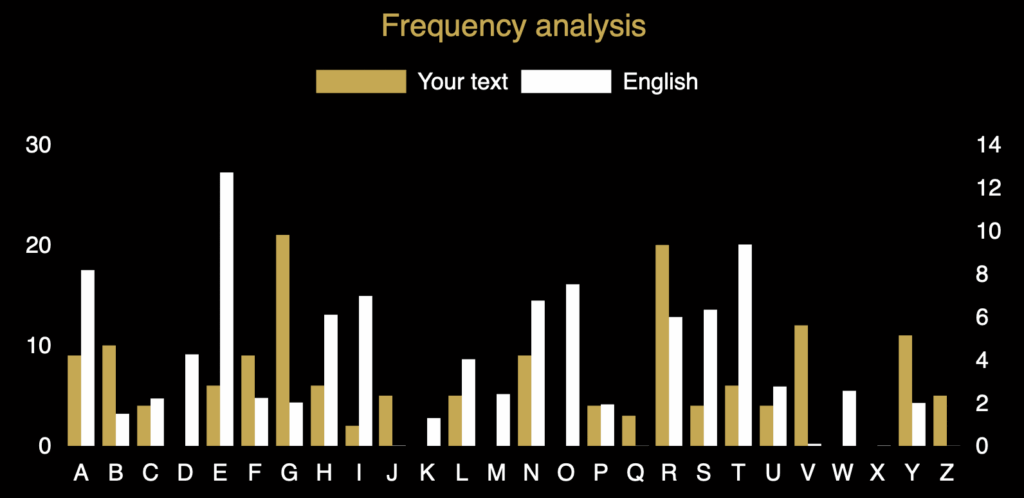
Are you still stuck on Challenge 4 part A? The blocking of the text into fives is an established trick to disguise the structure of a text and it can be remarkably effective in obfuscating (great word!) the plain text. Here a simple frequency count tells us a lot though. Notice the spikes at O and D in the cipher text (gold bars). They are clearly higher than the other peaks in the gold distribution. They are matched by peaks at E and T in the standard English distribution (white bars). What do you notice about the distances between the gold peaks and the white peaks? Does that suggest anything about the cipher that might have been used?
Case file 4.2
When I am trying to break an encrypted letter I always find the salutation and the signature very helpful. They are an excellent source of cribs. If we assume this is a letter, what names might fit? that surname is very distinctive. Do we know anyone in this story whose name has a letter appearing three times in it? A good guess here can unlock the rest of the cipher, and and you can use the substitution cipher tool on the cipher tools page (duh!) to help you break it.
Case file 4.3

Did you look at the frequency count we showed you yesterday? The highest peak at O in the cipher text probably means that it represents the most common letter in English, which is E, so the substitution probably converts E to O, which is a jump of ten (FGHIJKLMNO). The second highest peak at D might well represent T as that is often the second most common letter and gap from T to D is also ten! (UVWXYZABCD) This is very suggestive of a Caesar shift cipher, so it is worth heading over to the Caesar Cipher Tool to see if that breaks the cipher: https://www.cipherchallenge.org/tools/
Case file 4.4
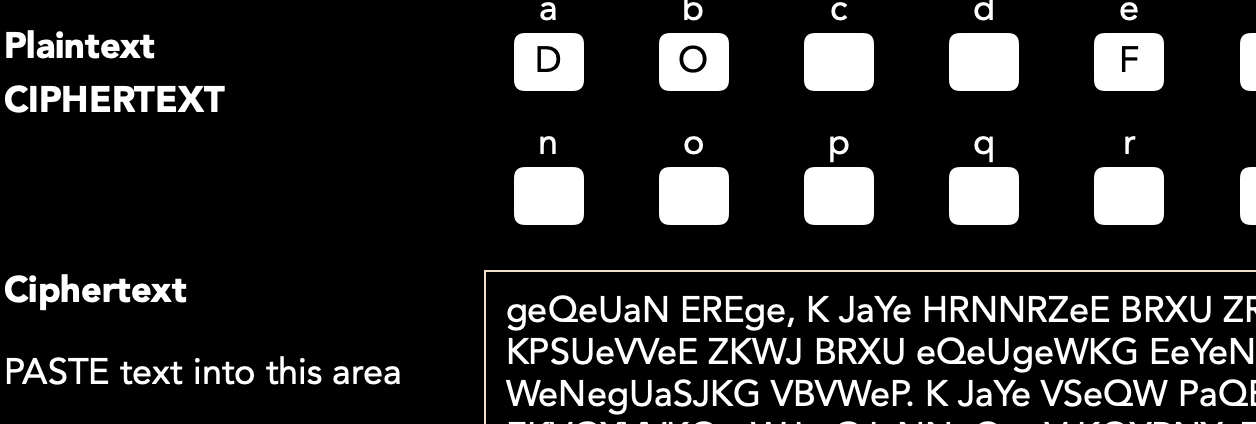
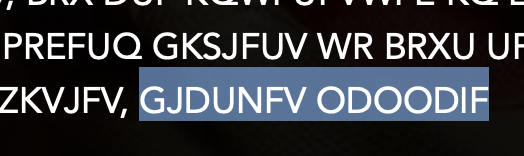
Did you guess right? Guessing is always worthwhile as a good guess can yield good evidence for a cipher. We have a number of characters in this story and if you make a list of their surnames you might spot that the one that has the same pattern ODOODIF is the name BABBAGE. If you guessed that, well done. If you enter that into the Substitution Tool on https://www.cipherchallenge.org/tools/ and paste the cipher text in the box below it the tool will start to decipher the text for you. If you look at the start of the message you might be able to guess some more letters! Entering them in the boxes above will break more of the cipher. For example the single letter K on its own must surely be an I or an A, and we already think that D stands for A so we can safely guess K stands for I. Try it and see what you can work out for yourselves!
Case file 5.1

It is always worth looking for a crib when you are unsure about what else to do. If you already worked out that the letter frequency distribution in 5 part A looks a lot like the standard distribution in plaintext then that should have given a strong hint that this might be a transposition cipher, and the best best way to break them is to look for a word that you might recognise, which you can use to try and figure out the permutation used. Looking at the start of this text we see letters that could be rearranged to give the name Molinaro, and while we can’t be certain which permutation has been been used just from that, there are not many that would work. What makes this a little tricky is that there are two possible O’s and two possible M’s that might have been used for the name, but a bit of trial and error should put you on the right track, especially if you can figure out how this message might have started!
Case file 5.2
Part B is in some ways a bit more straightforward than part A this week. The frequency counter shows that the plain text has most likely been encrypted using a substitution cipher and that the most common letters in the cipher text are O and then F. Searching for triples of the form F_O and O_F we see that FQO is common and therefore likely to stand for “the” which is an excellent start. While ti is not conclusive, it is also very suggestive that A appears almost exactly as often as “a” should appear, so it is also possible that A stands for a in the plaintext. Finally, S, B and M are the least commonly occurring letters in the cipher text, and given the frequencies shown on the standard frequency tables for English text, they probably stand for J, Q and Z in some order. That should be enough to get you started
Case file 6.1
Did you break Challenge 6A yet? If you did you will have learned that 6B is probably a Vigenere cipher. Those are hard to break unless you know the length of the keyword. You can read all about them in our BOSS Cryptanalyst Handbook. There are several ways to break these ciphers, one of them discovered by our friend Charles Babbage, but the more modern way is to compute the index of coincidence. Here is a great video to help you learn about the process!
Case file 6.2
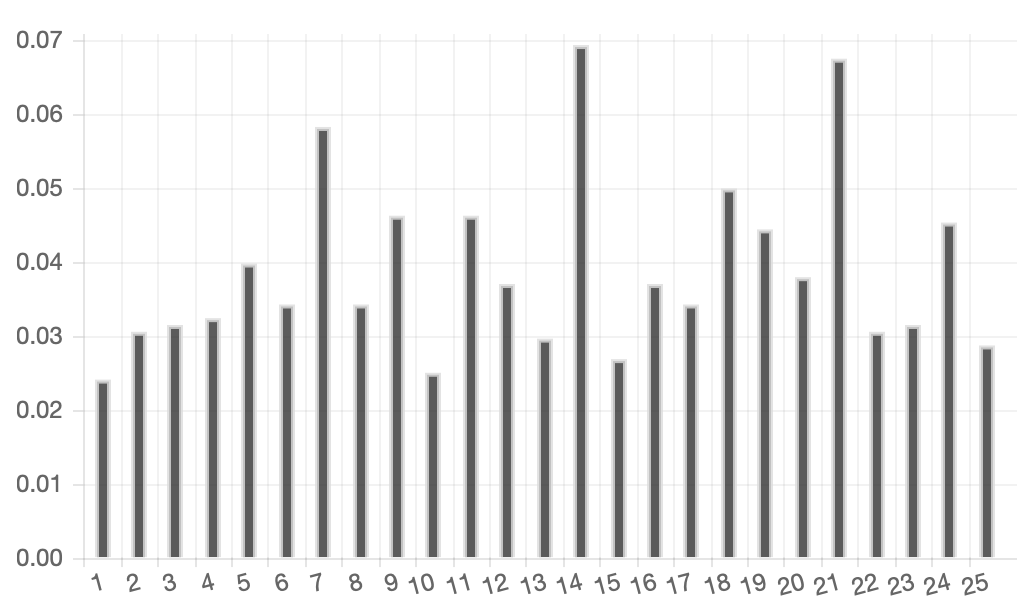
If you followed the video in Case File 6.1 you might have already computed the index of coincidence for the various possible key lengths for the Vigenere cipher in 6B, but if that is taking a little too long. Here they are already computed. As you can see there are peaks at length 7, 14 and 21 strongly suggesting one of those possibilities for the key length in the cipher. Given that it was almost certainly encrypted by hand, key length 7 is the most likely choice, so every 7th letter will have been encrypted with the same Caesar shift and you can use frequency analysis on those sets of letters to work out the keyword. Good luck.
Case file 6.3
In Case File 6.2 we worked out that the Vigenere keyword we are looking for has length 7, so we can treat the cipher as a collection of 7 different Caesar shift ciphers. The first one is used to encrypt the 1st, 8th, 15th, 22nd characters and so on, while the second encrypts the 2nd, 9th, 16th, 23rd … You get the idea. We can break these one at a time by using frequency analysis. Here we are trying to find the first Caesar shift so we are computing the frequencies of letters in positions 7k+1 using the app on our BOSS cipher tools page. A look at the table shows that G and R are the most common letters in those positions, so E is probably enciphered as one of those two letters for that shift. R results in the first character deciphering as M which is promising as a lot of the documents we have looked at start MY. That gives us a strong hint as to the second shift too. Could the ciphertext letter C stand for the plain text letter Y? That would imply that the shift for characters in positions 7k+2 would send E to I, and lo and behold, I is indeed one of the most common letter in those positions.
Case file 7.1

You already know that the key length for this Vigenere cipher is 7, so you just need to break the text into pieces and analyse them separately. I have started by showing you how to deduce the first letter of the key word, by analysing the 1st, 8th, 15th letter etc. to work out which shift is used for them. You can do the same for the 2nd, 9th and so on to get possibilities for the second letter of the keyword and work through the 3rd etc, to get all 7 shifts. Even if you make a mistake with some of them, carrying out those substitutions will help you to spot cribs that will then assist you in correcting the keyword! For the first letter we see that shift is likely to either carry E and T to L and W in some order. A shift of 18 does the trick so the key probably starts with S.
Case file 7.2
Computing the frequencies of letters in part B shows that the distribution is really too flat to be a mono alphabetic substitution or transposition cipher, or even a combination of those methods, so it is most likely to be a polyalphabetic cipher like part A. The tricky part is working out the length of the cipher key. If we are lucky that is the only tricky part and this will turn out to be another Vigenère Cipher, with key length of, say, 6?
Case file 8.1
| Key length | Index of Coincidence |
| 3 | 61.18 |
| 4 | 58.06 |
| 5 | 101.02 |
| 6 | 61.02 |
| 7 | 59.94 |
| 8 | 59.83 |
| 9 | 60.74 |
| 10 | 101.02 |
| 11 | 61.3 |
Since Challenge 8 part A is another Vignere cipher you need to work out the key length. Here are the indexes of coincidence for some potential key lengths in case you find that helpful!
Case file 8.2

Remember that messages between Babbage and Dodge are to be encrypted using a Playfair cipher, for which you need to complete a keyed grid. In this case the key is supposed to be taken from an agreed book, and Babbage has asked Dickens to tell Dodge the key. Luck is on our side because someone has attached the relevant page in the case file and that narrows down the possibilities a lot!
Case file 8.3

We can use the word structure to take a guess at a crib, and here I took a leap and guessed that the message began Dearest Grenville. That gives me some info about the Playfair substitutions as noted here. You should particularly note
DE->EG and LE->DG [really sorry about the typo earlier, Jodie]
which can only happen if these letters are all on the same line of the grid! You could also take a stab at the signature to get some more insight.
Case file 8.4
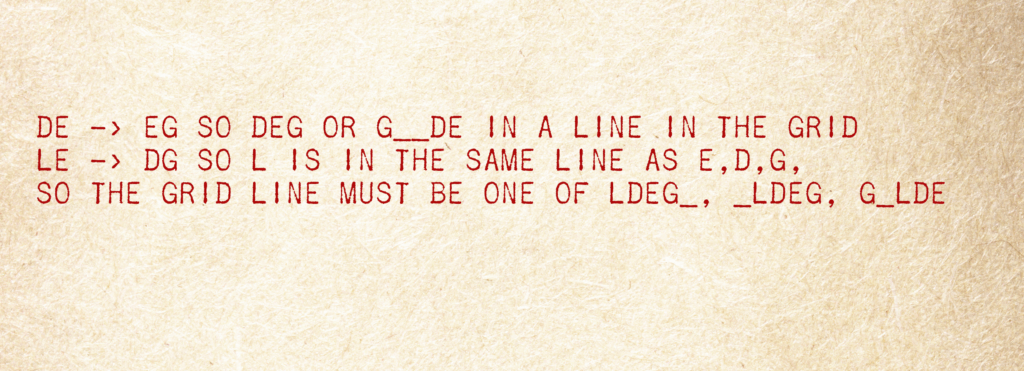
We saw that the letters D,E,L, G must be on the same line of the Playfair grid, but thinking about how the cipher encrypts pairs on a line, by shifting them one to the right, tells us more about the line they are in. Can you use that together with the page from which the key is taken to guess the key?
Case file 8.5
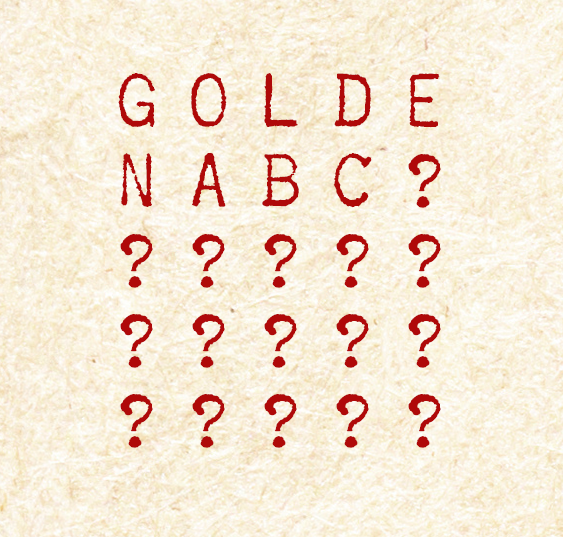
Putting together the insights we derived already I prepared the attached Playfair Grid. You should be able to use this to start to decipher the message and by the time you have finished you will be pretty much expert at using the cipher. Deciphering it without hints, might be a bit harder!
Case file 8.6
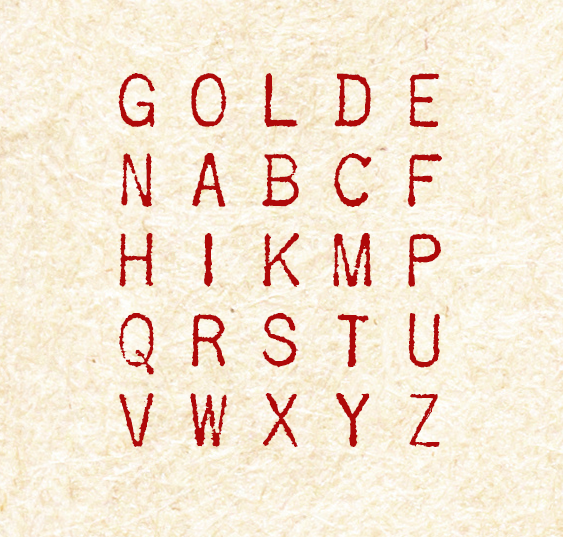
If you are still stuck, here is the completed Playfair Grid that Babbage has used to encipher his message to Grenville Dodge. You should practice using it to decipher the message (which is just the opposite of enciphering) so you get familiar with the idea.
Case file 9.1

From The Dickens Museum: “Dickens wore spectacles but he didn’t like people knowing. This is the only image of him wearing glasses. It’s a sketch by the caricaturist and portrait painter Sir Leslie Ward.”
Case file 9.2

The document in part A this week was believed to be a letter from Babbage to Dickens, which I found useful. When the cipher clerk who was handling it for me tried to break it she was very confused. She was pretty sure that she knew what cipher it was and how long the key must be, but even with a brute force through the dictionary she wasn’t getting English words out of the decrypt. It took me a minute to see why and hopefully you will get it too, but it may take a while to break this one. I will say that it is worth trying what you have already learned. It will get you at least half way there!.
Good luck, Jodie
Case file 9.3
I think you might be looking for this? Although unless you are very perspicacious I am not sure it will help much! Jodie
Case file 9.4
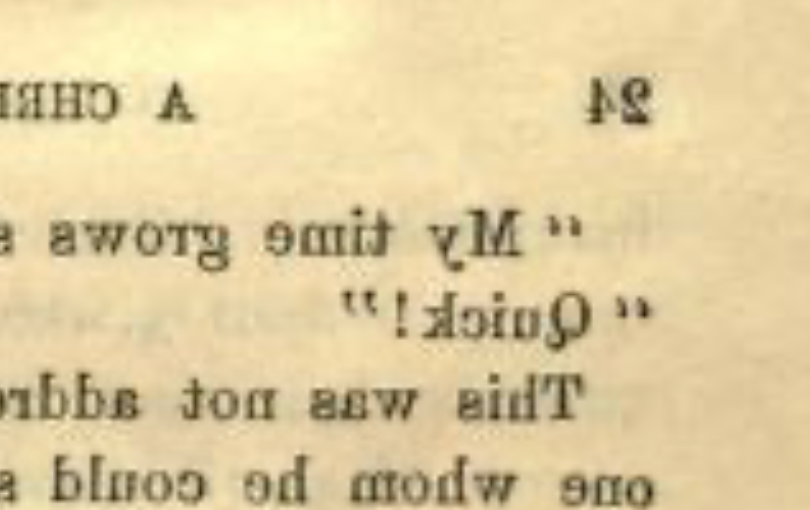
Did you “look back” at page number 24 to find the key? And did you find it?
Case file 9.5

If you finally realised that the keyword was on page 42 (not 24 – look back!) then you may have already found it, but if not then here is the Playfair grid. When you use it you will realise that something is not quite right, somehow the rules don’t entirely work! Hmmmm.
Case file 10.1

A deliberately obscure hint for 10 A. We will allow more tips through on the forum as we get them. Some may be cryptic (like this), some amusing, some might even be helpful. That is up to you!
Case file 10.2
Now to Challenge 10B – Like we always say, at least do something! Even if it isn’t obvious that it will work …
Case file 10.3
In the immortal words of Steve Jobs (at the 2007 launch of the first iPhone), “Are you getting it yet?”
Case file 10.4

Does this help? The clues will be a little less obscure from tomorrow, so make the most of it!
Case file 10.5

Case file 10.6

52 = 6^2 + 4^2. Now how do we start to fill in the rest of the grid?
Case file 10.7
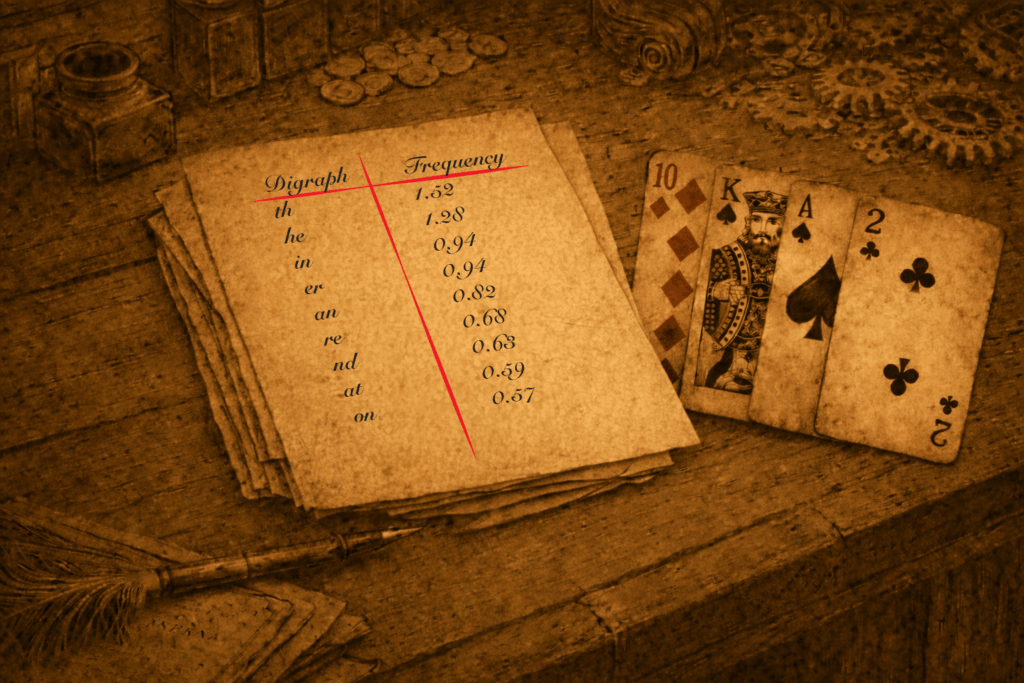
In a digraph cipher like this, frequency analysis is not quite as helpful as it is in a simple substitution, but it can still help. The most commendable digraph in English is “th” and helpfully that is also the most common digraph in the plaintext for this message. Given that this is some form of the foursquare cipher that should allow you to enter at least one of the plaintext pairs! After that the frequencies are not quite as helpful and you have to figure out what else you have that might help you fill in more of the grid!
Case file 10.8

Did you think of using the word “telegraph” as a crib? You should be able to assemble the pairs “ra” and “ph” in the grid from the cribs “th”, Babbage” and “REPORT” so if you can find the corresponding pattern in the text that should give you the pairs “el” and “eg” as well.
Case file 10.9

Did you spot this pattern in your partly deciphered text? It is very suggestive. Maybe you can even take a stab at one or both of the keywords in the grid now?
Case file 10.10

If you have been following along then you should have at least this much of the grid completed! Depth reading should help you to fill in the rest.
Case file 10.11
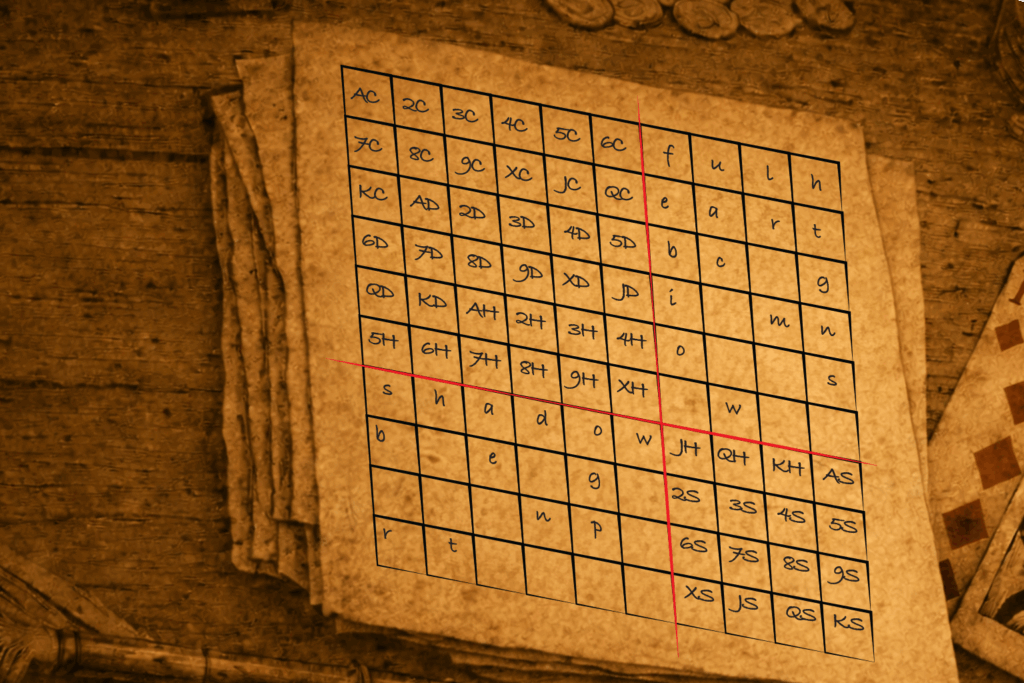
Did you find the keywords for the grid? Bonus points for finding them in A Christmas Carol! (not really, but you can feel pleased with yourself for reading it!)
Case file 10.12
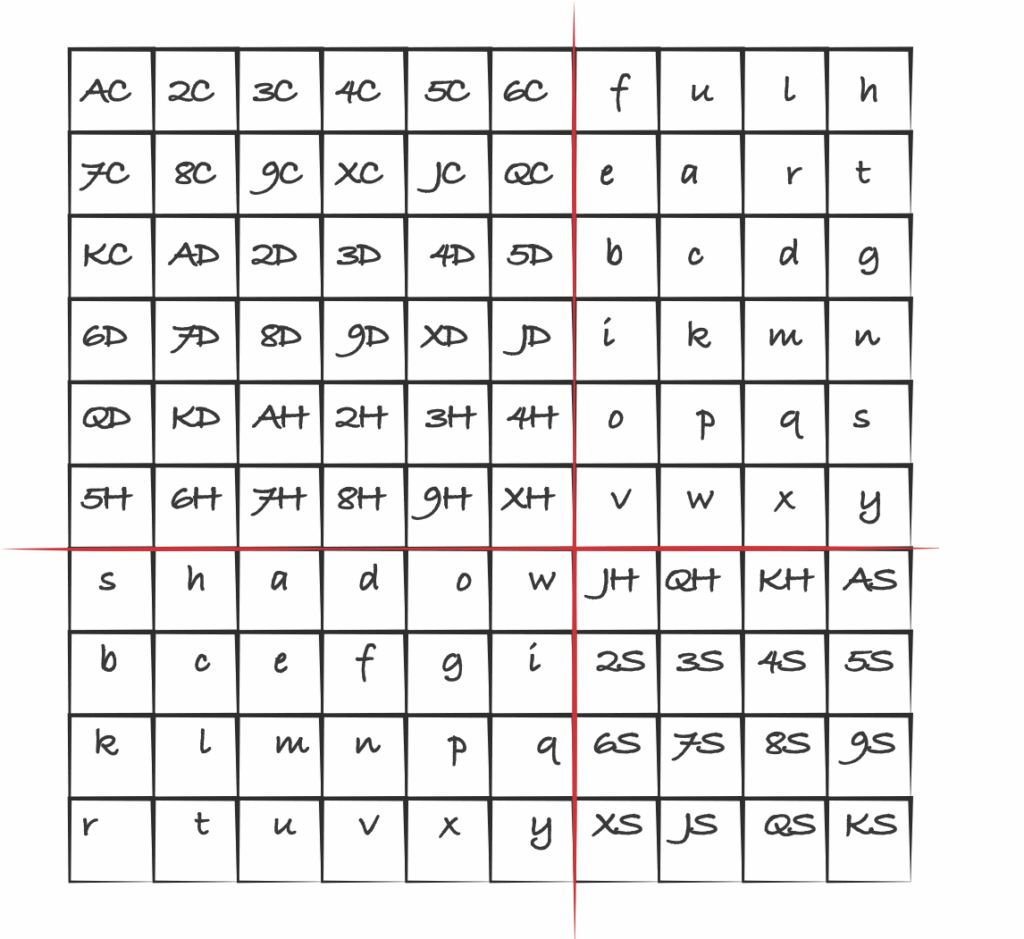
The final key grid. Now all you have to do is complete the decryption! Hope you enjoyed it (and Happy New Year!) Jodie

